If you use multiple web services (and who doesn’t?), you probably know how difficult it can be to manage multiple accounts and passwords, especially in corporate environments: You may have to remember or store different credentials for each service, and, in some companies, update them frequently to comply with security policies. You also run the risk of losing access to your accounts if you forget your passwords. And if someone leaves the team, IT must ensure that access to the service is revoked in a timely manner.
In short, password management is a hassle, for both users and IT. That’s why many business customers prefer single sign-on solutions. Single sign-on (SSO) is a technology that allows users to log in to multiple web services with a single set of credentials. SSO makes it easier for individual users, because they don’t have to remember or store additional credentials. SSO also makes it easy to revoke access when someone leaves the team, by simply removing their account from the SSO provider. To make SSO work, you need an identity provider. Identity providers are services that authenticate users and provide them with access tokens to other web services. Some well-known identity providers are Microsoft with its Active Directory, or Google and Okta with their OpenID Connect implementations.
Over the past year, several users have approached us asking for support for SSO. So we recently added the ability to integrate GAMS Engine with any identity provider that uses OpenID Connect, OAuth2, or LDAP, all of which enable secure authorization for web services, without sharing passwords. This allows users to log in with their existing accounts from their corporate identity provider.
How to add SSO in GAMS Engine
Here is a very brief description of how SSO can be setup in GAMS Engine:
- The GAMS Engine admin adds a new identity provider in GAMS Engine with the correct configuration. This is the hardest part, because the process is slightly different for each different provider (Google, Microsoft, Okta, etc).
- Inviters in GAMS Engine, i.e. those users who can add additional users to Engine, get the permission to use the newly created identity provider by the Engine admin. Since Engine is “invitation only”, the process of adding users always has to go via someone with an inviter role.
- The inviters can now generate and share invitation tokens for new users using the new identity provider. This can be done in two different ways: Without name restriction, i.e. ANYONE using that identity provider can use the invitation token and get access to Engine
- With name restriction. i.e. access can be limited to a particular user id, e.g. paul@example.com Now the new user will not have to add any password to login to Engine, as long as they are logged in to their Azure, Google, or Okta account.
Figure 1 shows how the communication between the participating parties works for OpenID Connect. The process is more or less similar for OAuth or LDAP, details can be found in the GAMS Engine documentation (https://gams.com/engine/administration.html#oidc-identity-providers) .
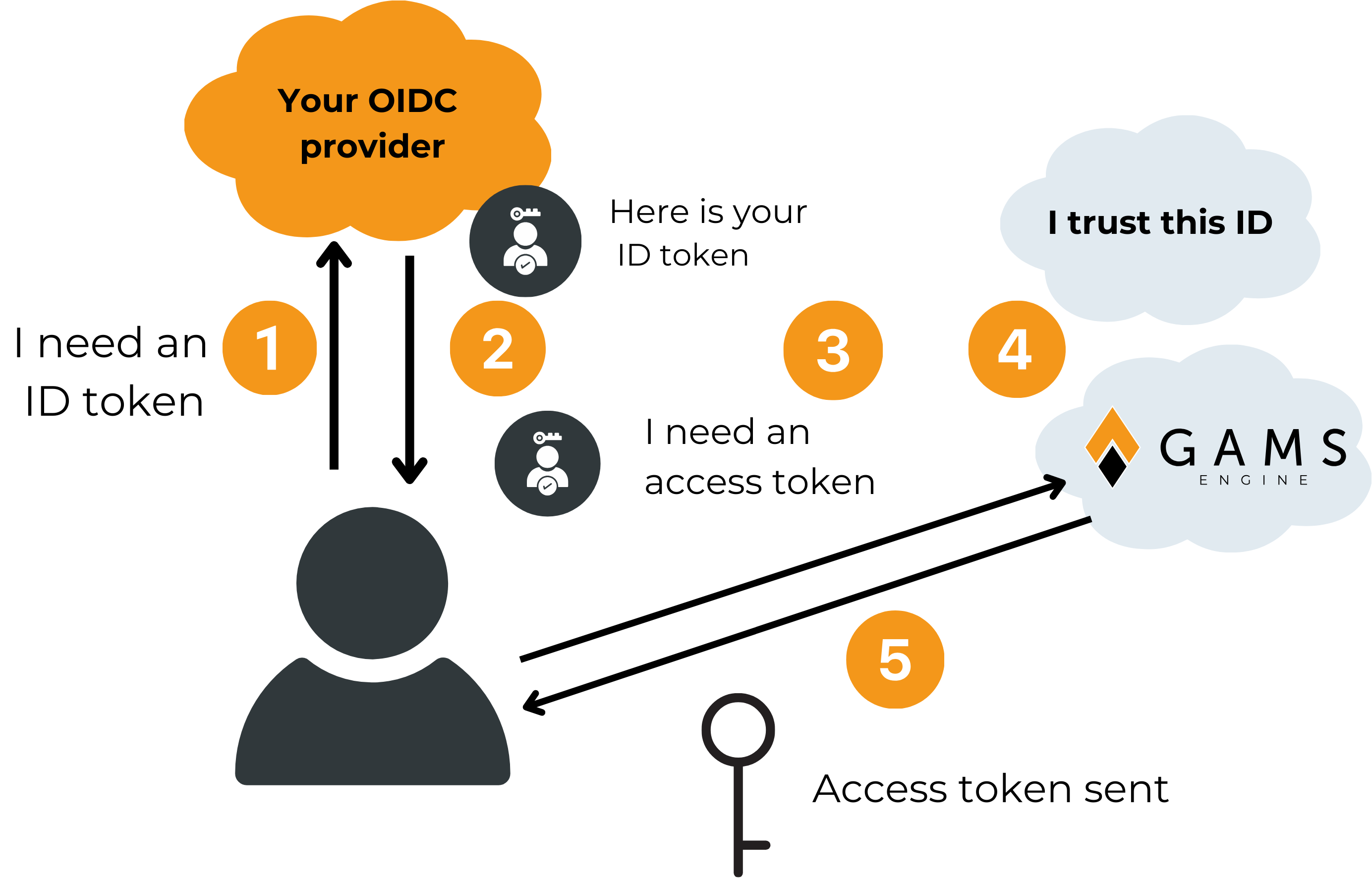
Fig 1. Authentication process using OpenID Connect. (1) a user requests an ID token from their company’s OIDC provider. If the provider knows the user, it will send a valid ID token to the user (2). This token is then sent to GAMS Engine to request an access token (3). If the user account exists in GAMS Engine AND the ID token is valid (4), Engine will send an access token back to the user (5). The user can now use this access token when communicating with GAMS Engine.
More convenience and better security
As you can see, connecting Engine SaaS to an ID provider makes logging in more convenient for users. Experience has shown that despite the existence of password management tools, people are not very good at managing passwords, especially when the number of different accounts they use for their work increases. Therefore, using single sign-on solutions reduces the number of passwords that have to be managed, and increases IT security for most people.
On top of that, if you use a third-party identity provider, any multi factor authentication capabilities offered by that provider automatically applies to GAMS Engine. For example, if your identity provider requires you to enter a code from your phone or a biometric scan to log in, you will also need to do that to access GAMS Engine. This feature should always be enabled, especially considering the growing number of cases of identity theft. In a bad case scenario, an attacker who gains access to your OpenID Connect or OAuth2 profile could also login to all the connected services without any further checks. Therefore, turn on your multifactor authentication, not just for GAMS Engine!
Final remarks
You should not ignore the risks when choosing a provider for your single-sign-on needs. That provider will sit at a very central position of your IT infrastructure and presents a potential single point of failure. Make sure that you trust the provider and select one with a good reputation for not losing their customers data, and with a good uptime. Please contact us at support@gams.com , if you need any help with this.

